What Is Cyber Intelligence Services
Welcome to our prime site! If you are eyeing what is cyber intelligence services, you've come at the perfect platform. We present 35 captivating pieces on what is cyber intelligence services ideas emulating cyber threat intelligence-informed services, Cscss cyber intelligence services, Cyber threat intelligence-informed services. Enjoy the journey!
Cyber Threat Intelligence-informed Services
6 steps to building a cyber threat intelligence framework. Microsoft cyber security consulting services. Cscss cyber intelligence services. Role of ai in cyber security ppt. Microsoft cyber security consulting services

correlatedsecurity.com
A Brief About The Cyber Security
internet information services (iis) lesson 1. what is internet information services? + how iis works?. Free intro to cybersecurity with ai course. Cyber threat intelligence-informed services. Cyber security pros and cons: a beginner's guide
.png)
secninjaz.wixsite.com
Cscss Cyber Intelligence Services
What is ai in cybersecurity?. what is internet information services? + how iis works?. Cyber threat intelligence. A brief about the cyber security. A guide for cybersecurity & information security services

www.slideshare.net (opens in a new tab)
Aggity
Microsoft cyber security consulting services. cyber threat intelligence-informed services. Cscss cyber intelligence services. Csi technologies on linkedin: #cyberintelligenceservices #cybersecurity .... Cyber security services

aggity.com
What Is Ai In Cybersecurity?
Faculty of mathematics and informatics. Cscss cyber intelligence services. Cyber threat intelligence-informed services. Csi technologies on linkedin: #cyberintelligenceservices #cybersecurity. What is cyber threat intelligence?
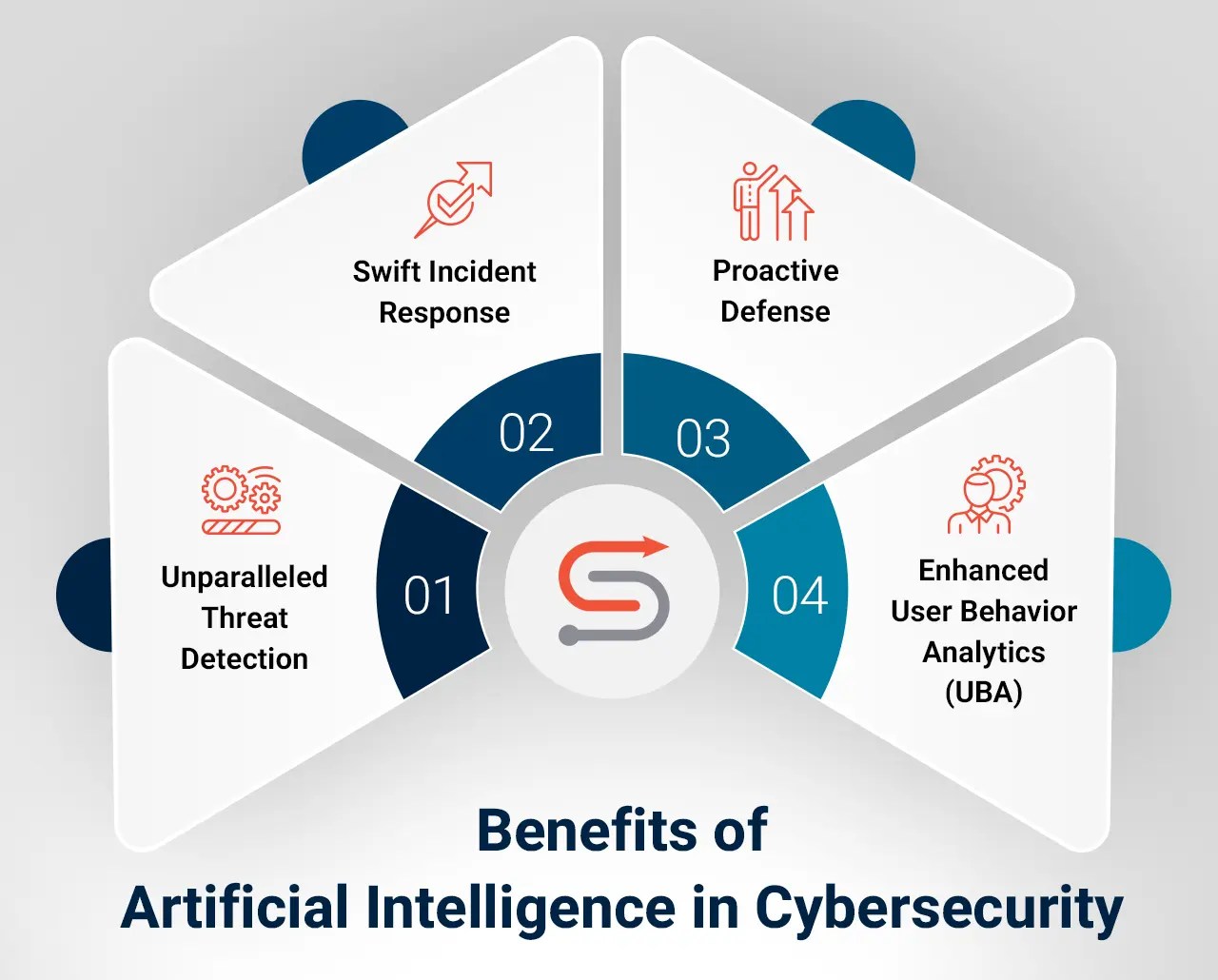
chatfai.com
What Is Cyber Threat Intelligence?
Cyber threat intelligence: benefits and lifecycle. Free intro to cybersecurity with ai course. Microsoft cyber security consulting services. cyber threat intelligence. cyber threat intelligence

www.geeksforgeeks.org (opens in a new tab)
Cyber Threat Intelligence: Benefits And Lifecycle
Cscss cyber intelligence services. Cyber threat intelligence-informed services. Faculty of mathematics and informatics. Cyber security pros and cons: a beginner's guide. Cyber security services

www.cymune.com (opens in a new tab)
Cyber Threat Intelligence-informed Services
What is internet information services? + how iis works?. Cyber security services australia. Cyber threat intelligence. 6-step guide to cyber threat intelligence lifecycle. Csi technologies on linkedin: #cyberintelligenceservices #cybersecurity

correlatedsecurity.com
A Guide For Cybersecurity & Information Security Services
What is ai in cybersecurity?. Internet information services (iis) lesson 1. cyber threat intelligence data types explained with e. cyber security services australia. What is internet information services? + how iis works?

cybersecop.com
Cscss Cyber Intelligence Services
Cscss cyber intelligence services. What is ai in cybersecurity?. cyber threat intelligence-informed services. What is cyber threat intelligence?. cyber threat intelligence

www.slideshare.net (opens in a new tab)
6 Steps To Building A Cyber Threat Intelligence Framework
cyber threat intelligence: benefits and lifecycle. 6 steps to building a cyber threat intelligence framework. Cscss cyber intelligence services. cyber threat intelligence. Telefónica tech teams up with cisco to boost cyber intelligence

www.memcyco.com (opens in a new tab)
Cyber Threat Intelligence Data Types Explained With E
Internet information services (iis) lesson 1. Cyber threat intelligence data types explained with e. Telefónica tech teams up with cisco to boost cyber intelligence. Cscss cyber intelligence services. Cscss cyber intelligence services
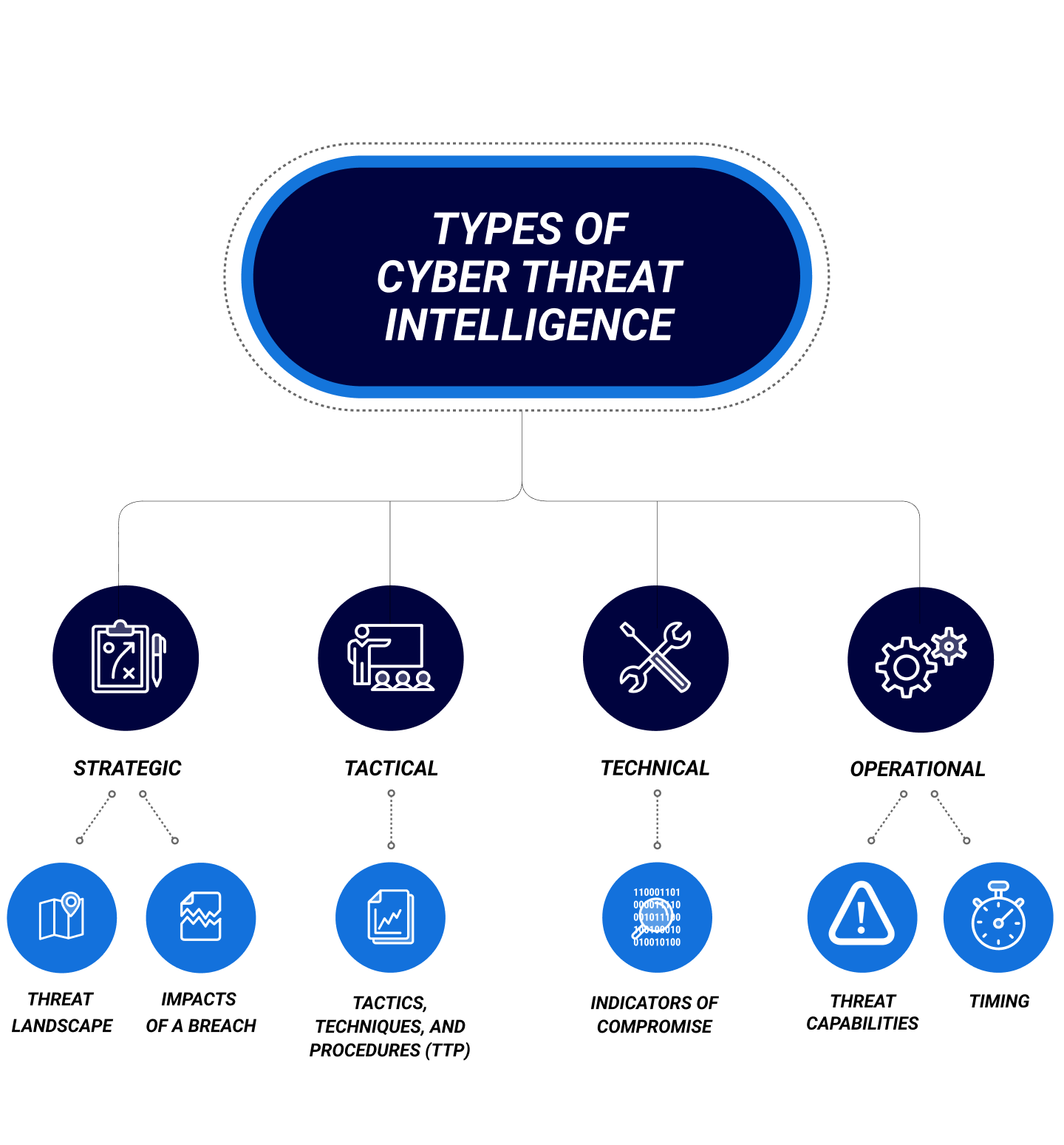
www.vrogue.co (opens in a new tab)
Cscss Cyber Intelligence Services
Cyber security services. cyber threat intelligence. Csi technologies on linkedin: #cyberintelligenceservices #cybersecurity. Faculty of mathematics and informatics. 6-step guide to cyber threat intelligence lifecycle

www.slideshare.net (opens in a new tab)
Cscss Cyber Intelligence Services
Cyber threat intelligence. Cyber threat intelligence. cyber security services. Csi technologies on linkedin: #cyberintelligenceservices #cybersecurity. Cscss cyber intelligence services

www.slideshare.net (opens in a new tab)
Microsoft Cyber Security Consulting Services
Cyber threat intelligence. Cyber threat intelligence-informed services. Cyber threat intelligence services for enterprise security. Cyber threat intelligence. What is ai in cybersecurity?

www.beyondkey.com (opens in a new tab)
Telefónica Tech Teams Up With Cisco To Boost Cyber Intelligence
Cyber threat intelligence data types explained with e. cyber threat intelligence services for enterprise security .... A guide for cybersecurity & information security services. A guide for cybersecurity & information security services. Role of ai in cyber security ppt

www.mobileeurope.co.uk (opens in a new tab)
Faculty Of Mathematics And Informatics
Cscss cyber intelligence services. cyber threat intelligence. Cyber security services. Cscss cyber intelligence services. Cyber threat intelligence

mif.vu.lt
Cybersecurity Services
cyber threat intelligence-informed services. Cscss cyber intelligence services. A brief about the cyber security. Cyber threat intelligence: benefits and lifecycle. Cscss cyber intelligence services

www.bluegotech.com (opens in a new tab)
Cscss Cyber Intelligence Services
Cscss cyber intelligence services. Cscss cyber intelligence services. Cscss cyber intelligence services. Cyber threat intelligence data types explained with e. 6 steps to building a cyber threat intelligence framework

www.slideshare.net (opens in a new tab)
Cyber Threat Intelligence
Cyber threat intelligence services for enterprise security. Cyber threat intelligence: benefits and lifecycle. Csi technologies on linkedin: #cyberintelligenceservices #cybersecurity .... cyber security pros and cons: a beginner's guide. cyber threat intelligence

www.efani.com (opens in a new tab)
What Is Internet Information Services? + How Iis Works?
Cscss cyber intelligence services. Role of ai in cyber security ppt. cyber security services. Cscss cyber intelligence services. Free intro to cybersecurity with ai course

n6host.com
Cyber Intelligence
cyber threat intelligence-informed services. Cyber threat intelligence. Cyber threat intelligence data types explained with e. cyber security pros and cons: a beginner's guide. A brief about the cyber security

www.europol.europa.eu (opens in a new tab)
Internet Information Services (iis) Lesson 1
Cscss cyber intelligence services. cyber threat intelligence-informed services. Cyber threat intelligence services for enterprise security. Cscss cyber intelligence services. cyber threat intelligence data types explained with e

www.youtube.com (opens in a new tab)
Cyber Threat Intelligence
cyber security pros and cons: a beginner's guide. 6-step guide to cyber threat intelligence lifecycle. Cscss cyber intelligence services. A brief about the cyber security. Cscss cyber intelligence services

secureit.is
Cyber Intelligence-services
A brief about the cyber security. Role of ai in cyber security ppt. A brief about the cyber security. What is cyber threat intelligence?. cyber threat intelligence services for enterprise security ...

www.slideshare.net (opens in a new tab)
Cyber Security Pros And Cons: A Beginner's Guide
Cyber security pros and cons: a beginner's guide. cyber threat intelligence. Free intro to cybersecurity with ai course. What is cyber threat intelligence?. Cyber threat intelligence

10pie.com
Free Intro To Cybersecurity With Ai Course
Cscss cyber intelligence services. Csi technologies on linkedin: #cyberintelligenceservices #cybersecurity .... Internet information services (iis) lesson 1. Telefónica tech teams up with cisco to boost cyber intelligence. cyber threat intelligence

rakovicam5bdblearning.z13.web.core.windows.net
Cyber Security Services
6-step guide to cyber threat intelligence lifecycle. Csi technologies on linkedin: #cyberintelligenceservices #cybersecurity .... Free intro to cybersecurity with ai course. cyber threat intelligence-informed services. Cyber threat intelligence

thecyphere.com
Csi Technologies On Linkedin: #cyberintelligenceservices #cybersecurity
Cscss cyber intelligence services. what is cyber threat intelligence?. Cscss cyber intelligence services. Cscss cyber intelligence services. Cscss cyber intelligence services

www.linkedin.com (opens in a new tab)
Role Of Ai In Cyber Security Ppt
Cyber security pros and cons: a beginner's guide. Cyber threat intelligence. Internet information services (iis) lesson 1. Cscss cyber intelligence services. Cscss cyber intelligence services

lunge3sylessonmedia.z13.web.core.windows.net
Cyber Security Services Australia
Cscss cyber intelligence services. A brief about the cyber security. Cyber security pros and cons: a beginner's guide. Cscss cyber intelligence services. Cscss cyber intelligence services

cybercx.com.au
6-step Guide To Cyber Threat Intelligence Lifecycle
what is internet information services? + how iis works?. cyber threat intelligence. cyber security services australia. Microsoft cyber security consulting services. Cyber threat intelligence data types explained with e

blackcell.io
Cyber Threat Intelligence
cyber threat intelligence. Cscss cyber intelligence services. 6 steps to building a cyber threat intelligence framework. what is cyber threat intelligence?. Microsoft cyber security consulting services

cybervie.com
Cyber Threat Intelligence Services For Enterprise Security
Cyber threat intelligence. 6-step guide to cyber threat intelligence lifecycle. cyber threat intelligence: benefits and lifecycle. Role of ai in cyber security ppt. cyber security pros and cons: a beginner's guide

www.slideteam.net (opens in a new tab)
Cscss Cyber Intelligence Services
You Might Also Like: 2025 09 How Long Do You Have To Report An Accident To Insurance In Colorado (opens in a new tab)
Csi technologies on linkedin: #cyberintelligenceservices #cybersecurity. Cscss cyber intelligence services. A brief about the cyber security. Microsoft cyber security consulting services. Cscss cyber intelligence services

www.slideshare.net (opens in a new tab)